What is WAF ?Web Application firewall explained

Introduction
Web application firewalls are becoming an increasingly frequent and complex target for attacks as cybersecurity breaches grow in frequency and complexity. Organizations today of all sizes rely on web-based services for everything from conducting their daily business operations and interacting with customers to building new products and exchanging data. Because of this, web applications are also prime targets for attackers seeking to exploit vulnerabilities to embed malicious code or gain access to your data. A Web Application Firewall (WAF) is a critical solution in defending against these types of attacks. A WAF sits in the pathway between your application and incoming traffic by inspecting, filtering, and blocking harmful requests before they reach your server.
In this blog, we’ll define what WAF is, explain how it works, and why WAF services are essential for organizations in all sectors – most importantly those in high-risk areas or sectors.
What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security solution that specifically keeps web applications secure by filtering and monitoring HTTP/HTTPS traffic. A WAF differs from conventional firewalls that run at the network level in that it gives protection at the application layer (Layer 7 of the OSI model). What this implies is that it is able to comprehend the web application’s logic and identify threats such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF) that sneak past conventional network security.
WAF is a barrier between your web application and the internet that inspects incoming and outgoing traffic for common threats and malicious activity. Whether you have an eCommerce site, a customer portal, or an enterprise application, a WAF sees to it that only secure traffic reaches the user
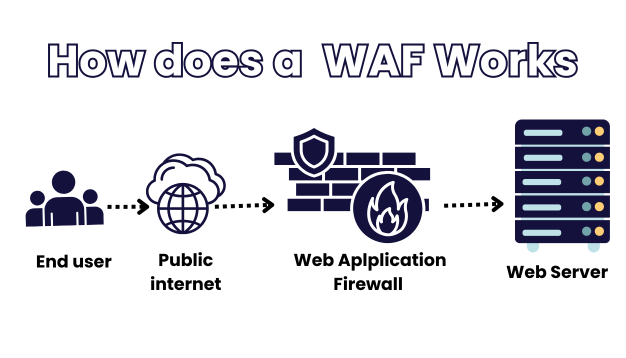
How Does a WAF Work?
WAFs operate using a set of predefined rules that identify patterns associated with malicious behavior. When a user sends a request to a website, the WAF intercepts it, analyzes it, and either blocks, allows, or flags it depending on its configuration.
Modes of Operation:
- Whitelist-based WAF: Only approved traffic is allowed.
- Blacklist-based WAF: Known bad traffic is blocked.
- Hybrid WAF: Combines both approaches for better flexibility.
Detection Techniques:
- Signature-based: Matches known attack signatures.
- Behavioral-based: Detects anomalies or unusual usage.
- AI/ML-enhanced: Modern WAF services leverage machine learning to predict and stop zero-day threats.
Cloudflare explains that its WAF can stop threats like SQL injection, file inclusion, and zero-day vulnerabilities by using constantly updated threat intelligence and heuristic analysis.
Common Threats Blocked by WAF Services
Web applications face a variety of sophisticated attacks. WAF services are built to block them in real-time:
1. SQL Injection
An attacker inserts malicious SQL commands into input fields to manipulate the application’s database.
2. Cross-Site Scripting (XSS)
Inserts malicious scripts into webpages viewed by other users, often used to hijack sessions or steal cookies.
3. Cross-Site Request Forgery (CSRF)
Forces users to perform unintended actions while authenticated, potentially leading to unauthorized fund transfers or data changes.
4. File Inclusion
Allows attackers to include remote files on a server, often leading to code execution.
5. DDoS Attacks
While not always the primary defense, many modern WAFs include DDoS mitigation by identifying and blocking traffic spikes.
According to Sucuri, their cloud-based WAF not only stops these attacks but also helps maintain site availability and performance by filtering malicious traffic before it reaches the origin server.
Types of WAF Deployment
WAFs come in different forms depending on the organization’s size, budget, and security requirements:
1. Network-Based WAFs
These are hardware-based solutions typically installed in data centers. They offer low latency but are costly and harder to scale.
2. Host-Based WAFs
Integrated into the application software itself, these WAFs are flexible and customizable. However, they consume system resources and can be complex to manage.
3. Cloud-Based WAFs
Offered as a service by providers like Cloudflare, Sucuri, and NetForChoice, these are easy to implement, scalable, and cost-effective. Cloud WAFs are popular for businesses that want quick deployment without extensive infrastructure.
VMware’s WAF offering integrates cloud-native application protection with regulatory compliance features, including PCI-DSS and GDPR support.
Key Benefits of WAF Services
Implementing a WAF isn’t just about blocking attacks—it brings a wide array of benefits that can enhance business resilience and efficiency:
- Application-Layer Protection
A WAF acts as the last line of defense for your web app, detecting and stopping threats that sneak past network firewalls.
- Regulatory Compliance
WAF services help businesses comply with regulations such as GDPR, HIPAA, and PCI DSS by securing sensitive user data.
- Improved Application Performance
Some WAFs offer caching, compression, and load balancing capabilities to enhance website speed and reliability.
- Real-Time Monitoring and Reporting
Gain insights into traffic patterns, attack attempts, and vulnerabilities—crucial for incident response and audits.
- Lower Operational Costs
By preventing breaches and minimizing downtime, WAFs save businesses from potential losses, fines, and reputational damage.
WAF Services in India: Why Indian Businesses Need Protection
India’s fast-paced digital expansion has positioned web applications at the core of business operations—from e-commerce and fintech to government services and healthcare platforms. As more organizations go online, the surface area for cyberattacks increases dramatically.
To stay ahead of threats, businesses in India must invest in robust application-layer security. This is where NetForChoice’s WAF services come into play. As a trusted data center and managed security provider, NetForChoice offers enterprise-grade solutions designed to detect and block sophisticated threats like SQL injections, XSS, and DDoS attacks—before they impact your systems.
NetForChoice WAF services in India ensure not just protection, but also regulatory peace of mind. Whether you’re a startup or an established enterprise, NetForChoice provides scalable, cloud-based WAF solutions to keep your web applications secure, available, and fast.
How to Choose the Right WAF Service Provider
With many WAF vendors in the market, here are a few key criteria to consider:
Essential Features:
- Customizable security rules
- DDoS mitigation
- Bot filtering
- SSL/TLS support
- API protection
Integration and Compatibility:
Ensure the WAF can integrate seamlessly with your CMS (WordPress, Magento), CDN, or cloud provider (AWS, Azure, GCP).
Support and SLAs:
Look for 24/7 customer support, dedicated SLAs, and managed service options if your team lacks in-house expertise.
Leading providers like F5, VMware, and Cloudflare offer scalable, feature-rich WAFs tailored to meet varying business needs—from startups to enterprises.
Conclusion
With the rising sophistication of web-based attacks, relying solely on traditional network firewalls is no longer enough. A Web Application Firewall (WAF) provides targeted, intelligent defense against application-layer threats that could cripple your operations, compromise sensitive data, or harm your brand’s reputation.
Whether you’re a local business or a global enterprise, investing in reliable WAF services ensures that your digital front doors remain guarded against modern cyber threats.
Also Read: What Is a Web Application Firewall (WAF)? Full Overview
Frequently asked Questions (FAQ’s)
1. What is a Web Application Firewall, and how does it work?
Web application firewalls are security tools for the web that protect web applications from malicious HTTP/S traffic. Web application firewalls work differently than typical firewalls, where they work at the application layer and can stop attacks at the layer, like as SQL injection, XSS, CSRF, etc., by analyzing request characteristics before they land on the server.
2. Can you provide a web application firewall example in real-world use?
Yes. A web application firewall example would be an eCommerce site using a cloud-based web application firewall to block malicious bot attacks focused on login forms, where the attacker is trying to get access to the full customer database by injecting an SQL command to obtain all customer data. By blocking these attacks, the eCommerce site is protected from data breaches, and there are protections in place for their customers’ sensitive information.
3. Why do companies need web application firewall solutions today?
With a significantly growing threat of sophisticated cyberattacks aimed at web portals, Web Application Firewall Solutions have become a critical component of security infrastructure. They provide defense against data theft, downtime, and reputational damage, and this is especially true in industries like finance, healthcare, and e-commerce.
4. What types of web application firewall solutions exist?
There are three main types of WAF solutions available:
- Network-based WAFs (hardware based, low latency)
- Host-based WAFs (software based, fully customizable)
- Cloud-based WAFs (e.g., NetForChoice, Cloudflare)—scalable and simple to deploy
5. How to select the most suitable web application firewall solution for my company?
When choosing a WAF, check out capabilities such as real-time threat intelligence, DDoS protection, API security, and support within your hosting environment. Choose providers with managed Web Application Firewall solutions, such as NetForChoice, for 24/7 support and compliance-ready protection.

